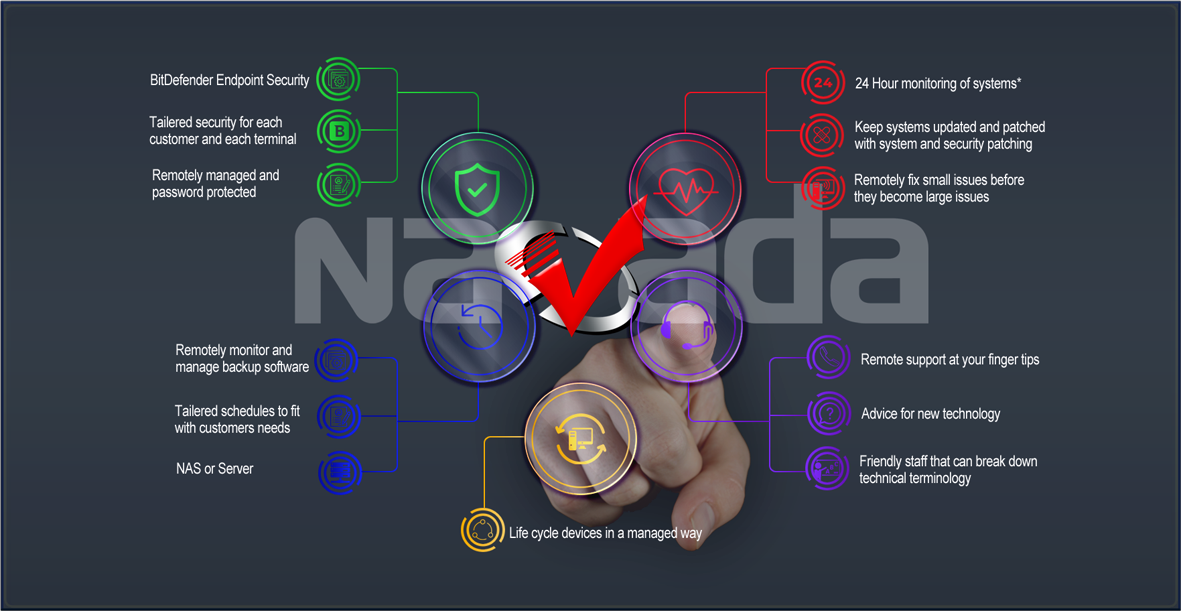
 BitDefender Endpoint Security Bitdefender HyperDetect contains machine learning models and stealth attack detection technology. It forms an additional layer of security, specifically designed to detect advanced attacks and suspicious activities in the pre-execution stage.
BitDefender Endpoint Security Bitdefender HyperDetect contains machine learning models and stealth attack detection technology. It forms an additional layer of security, specifically designed to detect advanced attacks and suspicious activities in the pre-execution stage. Tailored security policies Many features work together to reduce the attack surface: Patch Management, Full Disk Encryption, Web Threat Protection, Firewall, Application & Device Control.
Tailored security policies Many features work together to reduce the attack surface: Patch Management, Full Disk Encryption, Web Threat Protection, Firewall, Application & Device Control. Securely administered protection Authorised and authenticated users only can edit policies and have the ability to remove the software, adding another layer of protection.
Securely administered protection Authorised and authenticated users only can edit policies and have the ability to remove the software, adding another layer of protection. Life cycle devices Understanding the key stages in a computer's life cycle will help you to plan future IT acquisitions and identify the point at which maintaining your old technology is no longer cost effective.
Life cycle devices Understanding the key stages in a computer's life cycle will help you to plan future IT acquisitions and identify the point at which maintaining your old technology is no longer cost effective.
 Tailored backup Create tailored backups around your needs, drive rotation and hardware.
Tailored backup Create tailored backups around your needs, drive rotation and hardware. For both Server and NAS systems Using a range or backup softwares and devices to keep date safe for Windows Server, QNAP NAS or Synology NAS and possibly terminals.
For both Server and NAS systems Using a range or backup softwares and devices to keep date safe for Windows Server, QNAP NAS or Synology NAS and possibly terminals.  Remotely Administered backup Error Monitoring for all backup devices is an essential part of business and should not be overlooked. Backup systems rely on software and hardware so failures happen, proactive maintenance keeps businesses safe.
Remotely Administered backup Error Monitoring for all backup devices is an essential part of business and should not be overlooked. Backup systems rely on software and hardware so failures happen, proactive maintenance keeps businesses safe.
 Friendly staff Ready to help staff that explain technical terms for customers to understand so we overcome issues and have the same kind of understanding about a situation.
Friendly staff Ready to help staff that explain technical terms for customers to understand so we overcome issues and have the same kind of understanding about a situation.  Advice for new technology When approaching new technology, we follow a bigger picture approach keeping eyes on ultimate goals but still have the ability to see the pit falls, please seek advice with all new technology so you don't waste time and money.
Advice for new technology When approaching new technology, we follow a bigger picture approach keeping eyes on ultimate goals but still have the ability to see the pit falls, please seek advice with all new technology so you don't waste time and money.  Remote support at your fingertips Faster response time, minimised IT cost, focus on business, increased productivity, proactive system maintenance.
Remote support at your fingertips Faster response time, minimised IT cost, focus on business, increased productivity, proactive system maintenance.
 Remotely fix small issues Fixing small issues that take a small amount of time pay dividends, when left can become crytical and time consuming leading to loss of productivity.
Remotely fix small issues Fixing small issues that take a small amount of time pay dividends, when left can become crytical and time consuming leading to loss of productivity.  Keep devices updated Software updates are important because they often include critical patches to security holes. Newly discovered vulnerabilties are patched on average 70-100 days after discovery. Close the vulnerable window as fast as possible
Keep devices updated Software updates are important because they often include critical patches to security holes. Newly discovered vulnerabilties are patched on average 70-100 days after discovery. Close the vulnerable window as fast as possible 24 Hour monitoring of systems* constant Health monitoring and installing patches when you are not there, allows for greater productivity during the day. Alerting us immediately when symptoms occur allowing to stay ahead of outages. *Computers must be on.
24 Hour monitoring of systems* constant Health monitoring and installing patches when you are not there, allows for greater productivity during the day. Alerting us immediately when symptoms occur allowing to stay ahead of outages. *Computers must be on.
All aspects of your IT infastruture are important. Keeping systems running so productivity is kept in peak performance. Patching systems from vulnerabilities as soon as they are released. Keeping systems secure to keep the bad guys out. Doing everything possible to protect your business and if by chance it all goes horribly wrong, have backups to restore and get you back to peak performance asap. - That is what we do.
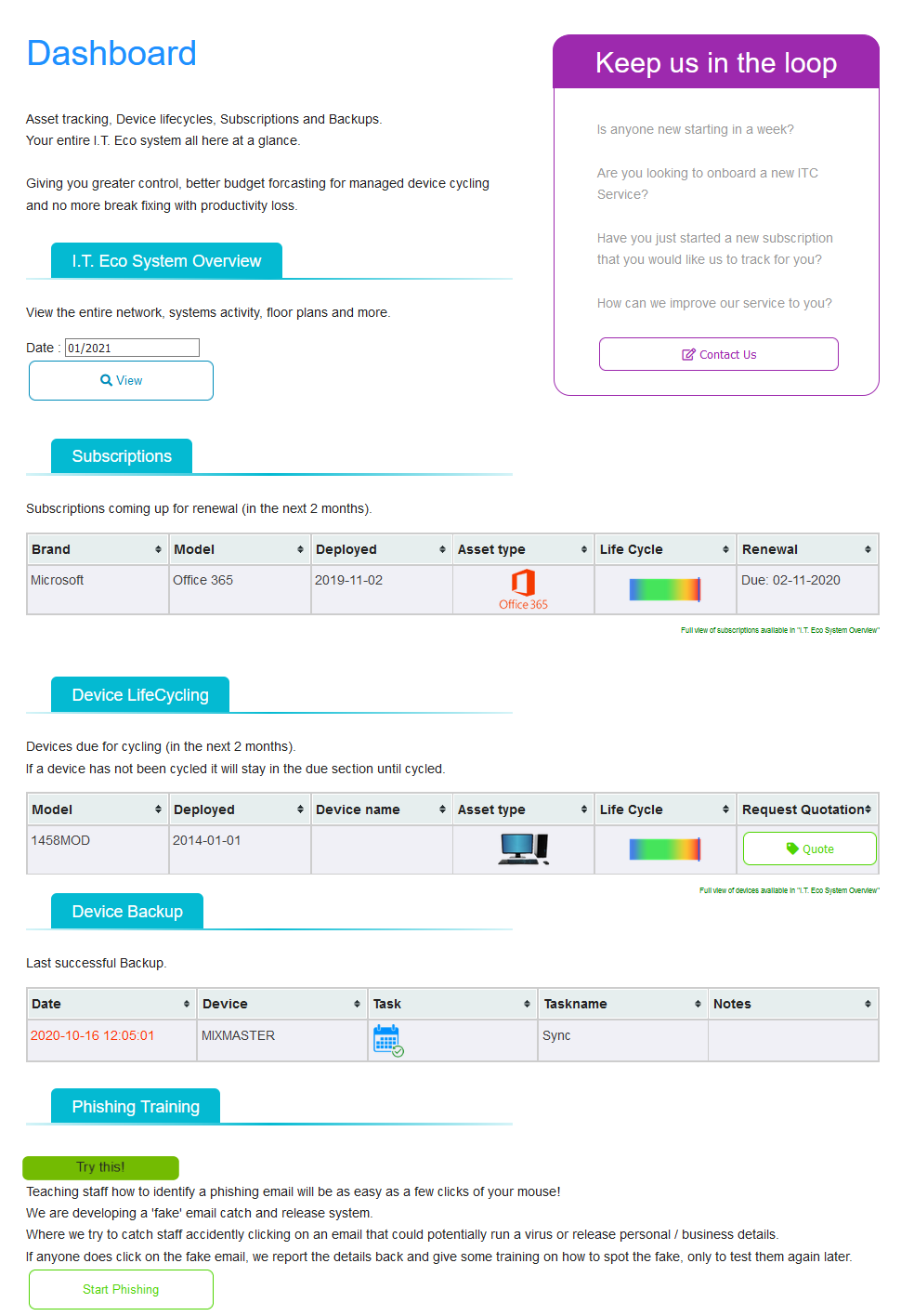
Each customer with get their own navada dashboard to show at a glance important information.
System Reports
- An in depth view of your IT eco system, network, floor map and performance.
Subscriptions
- Office 365, Adobe Creative Cloud or other subscriptions are monitored.
Device lifecycling
- Helping to keep your IT budget on track, systems due are listed here and can easily be quoted to replace by the click of a button.
Device Backup
- For peace of mind, you can check when your last successful backup was with color coded date to show urgency.
Staff Phishing Training
- Teach staff to recognise a phishing email to help your business keep safe from exposing usernames, passwords and malware encryption.
Enquire Today














